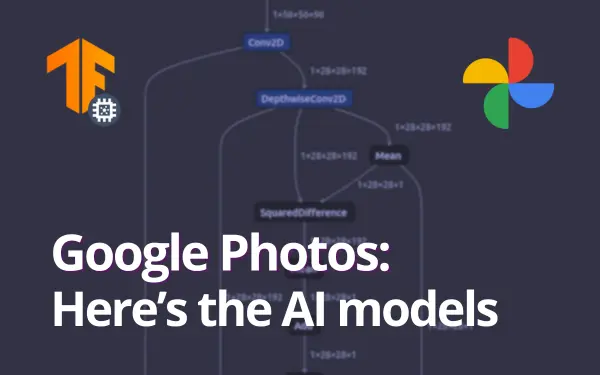
Google Photos is one of the most widely-used photo management applications globally, pre-installed on almost every Android device running Google...
Secure AI Models
Transform your AI models into safe and valuable assets.
Our Solutions
Prevent Copy and Reuse of Your
Proprietary Algorithms
AI Protection
Secure your on-device AI models against reverse engineering with a low computing footprint. Protect your competitive edge and technological advance.
AI Licensing
Deploy, manage, and monetize your AI models with confidence. Protect your intellectual property and supercharge profits.
AI Watermarking
AI Watermaking is coming soon! Enhance your AI models with robust watermarking to safeguard against unauthorized use and distribution.
How It Works
Discover Our Solution for On-Device AI Security
Awards

Marie Paindavoine wins the first #WomenInTech award, celebrating women entrepreneurs shaping the future of tech in Europe, organized by Wavestone and Les Echos.

Skyld won the Access-2-Finance Award during European Cyber Week 2023, recognizing us as one of the top cybersecurity startups in Europe.
Marie Paindavoine, founder and CEO, won the European Cyber Woman Award in the Entrepreneur category, recognizing her impact in AI and cybersecurity.

We were honored to be among the 12 most promising cybersecurity startups in Europe, reaching the finals of the ECSO Startup Award 2024.
FAQ
Your AI model is likely to be extracted whenever it is deployed on untrusted environnements: on the Edge, on IoT devices, on Smartphones and tablets, on desktop applications, on browsers and on-premises servers. It is also possible for the cloud provider to access the model.
Yes, it’s relatively easy to extract an on device AI model if security measures are not sufficiently robust. Through decompilation, an attacker can locate and extract the AI model. Even if the model is encrypted, it can be recovered with dynamic analysis: an attacker just needs to wait for the decryption before inference.
The most direct consequence is the theft of intellectual property. If an AI model is successfully reverse-engineered, it can be reused directly, or fine-tuned to fit the attacker purpose. Furthermore, access to the AI model facilitates more advanced attacks such as adversarial examples and model inversion. You can learn more about model inversion attack by reading this article.
Encryption is easy to deploy but is also easy to bypass. Indeed, even if the model is encrypted when it’s stored, it may still be vulnerable to runtime attack as it must be decrypted for inference. An attacker can stop the application execution at the decryption step and recover the entire model.
Skyld protects AI models everywhere they are executed. Our developed techniques prevent the software analysis and relevant AI attacks from getting models key information, especially the weights. We apply robust linear algebra transformations, so that the explicit parameter information cannot be extracted from the on-device AI model file. These transformations ensure that models are protected during runtime even on GPUs.
As OS: Android, Linux, Windows and as ML inference frameworks: ONNX, Tensorflow(lite), Keras.
Skyld protects different kinds of neural networks : CNN, RNN, LSTM, Transformers and Vision Transformers, LLM. To request the list of all the tested models, please contact us.
Our protection has no impact on model accuracy. As for performance, this depends on the specific architecture of the model used, generally below 20% overhead. Contact us us for your specific use case.
Our tech blog
Here Are Our Latest Articles

Read More
New Deployments, New Threats: How To Protect Local AI...
Introduction: The Rise of Local AI

Read More
Attack On AI Models: What You Need to Know!...
Artificial intelligence is used in many fields, including autonomous cars and facial recognition. Every AI application has a carefully designed...
Read More
What Are the Three Types of Artificial Intelligence and...
First Type Of Machine Learning Models: Supervised

Read More
How Do You Reverse-engineer An Android App?
The world of Android applications is constantly evolving, offering a myriad of features to users worldwide. However, this diversity and...

Read More
In Which Applications Are ML Models Hidden?
Artificial Intelligence (AI) and Machine Learning (ML) have rapidly evolved to become essential components of many applications we use daily....

Read More
Artificial Intelligence Model Extraction
What is a model and why do we care? Machine learning models are the results of highly complex computations and...

Read More
Model Inversion Attacks: Safeguarding Your AI Secrets With Skyld...
Have you ever wondered if your machine learning models are vulnerable to attacks that can extract sensitive information, revealing the...

Read More
Protect Your On-Device Artificial Intelligence Algorithms: Encryption Is Not...
On-Device Artificial Intelligence (AI) is an invaluable asset to many industries, offering revolutionary capabilities in analysis and prediction. However, with...

Read More
Expert Series : Thibault Maho.
After working at xBrain, Thibault Maho started a Ph.D. whose title you may not understand: « Input Space Exploration for...
Our News
Here Are Our Latest News.

Read More
Season 7 Of The Women Entrepreneurs Program by Orange...
March 2025 marked the start of Season 7 of the Women Entrepreneurs Program. Led by Orange, this program supports women-led...
Read More
Skyld joins the Female Founders Fellowship at STATION F...
We are proud to announce that Skyld is now part of the Female Founders Fellowship at STATION F, the world’s...

Read More
Skyld Wins the #WomenInTech Award: A Big Step for...
On March 6, Marie Paindavoine, founder of Skyld, won the very first #WomenInTech award, organized by Wavestone and Les Echos....

Read More
Marie Paindavoine Has Been Selected As One Of The...
Marie Paindavoine, CEO of Skyld, is included in the list of the 100 innovators of 2025 by Le Point. This...

Read More
Skyld on the Red Carpet: Review of WAICF 2025...
From February 13 to 15, 2025, the Palais des Festivals et des Congrès in Cannes hosted the 4th edition of...

Read More
Skyld at AI Business Day: The Summit for Action...
The AI Business Day, part of the AI Action Summit organized under the Élysée’s patronage, has become the must-attend event...

Read More
Marie Paindavoine Joins Women TechEU Program: A Recognition For...
2025 is off to a great start for Skyld! We are excited to announce that Marie Paindavoine, our CEO, is...

Read More
3rd Edition of the Research Winter School by CyberSchool...
On February 6, 2025, Sklyd took part in the 3rd edition of the École d’Hiver Recherche. The event was organized...

Read More
13 French Startups to Watch And Skyld Is On...
Skyld is featured in the prestigious list of “13 French startups to watch outside of Paris, according to VCs” by...

Read More
In The Spotlight: Marie Paindavoine Wins The Cyber Woman...
On December 10th in Paris, women in cybersecurity were celebrated!

Read More
Imagine Summit: A Day Focused on Innovation
The 9th Imagine Summit just came to a close! Organized by Le Poool and La French Tech Rennes St-Malo, in...

Read More
GenerationAI: A Vision of AI Beyond Algorithms
On December 3rd, our CEO Marie Paindavoine was at GenerationAI Paris 2024, giving a presentation on “Model Extraction: Why You...

Read More
Skyld Joins The New Season Of Thales Cyber@Station F...
The Thales Cyber@Station F acceleration program is a great opportunity for Sklyd to benefit from Thales’ expertise and ecosystem.

Read More
We're Now Part Of The NVIDIA's Inception Program For...
We are excited to announce that we have been accepted into NVIDIA’s Inception Program, which supports start-ups in AI and...

Read More
Skyld At VivaTech 2024
VivaTech opened its doors on Wednesday, May 22, 2024, and ran until May 25. This 8th edition brought together technology...
Read More
In Wavestone's Radar!
Skyld is proud to be listed on the Wavestone radar of French cybersecurity start-ups 2024 in the Artificial Intelligence category....

Read More
Skyld, The Nominated Startup, Wins The Audience Award At...
The Halle de la Brasserie in Rennes was the stage for an event, the Creators' Morning, bringing together nearly 250...

Read More
Skyld At The ECSO Startup Award Finals Which Took...
What an exciting adventure Skyld embarked on by participating in the finals of the European Cyber Security Organisation (ECSO) Startup...

Read More
Skyld In The Spotlight for The 38th Edition Of...
Every year, this prestigious event highlights exceptional businesses, emphasizing their achievements in crucial areas such as societal engagement, innovation, responsible...

Read More
Flashback To Our Participation At WAICF At The Palais...
A few weeks ago, the Skyld team had the exceptional opportunity to participate in the World Artificial Intelligence Cannes Festival...